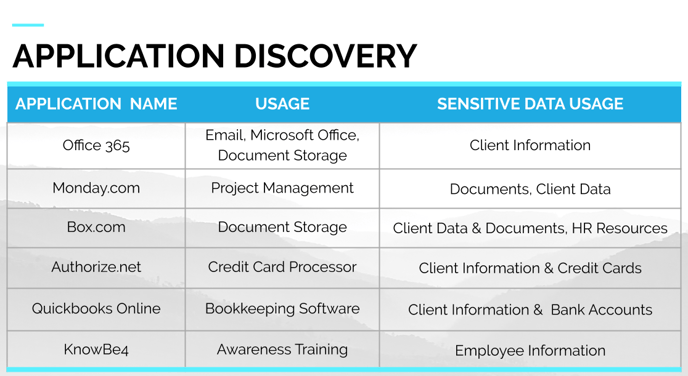
The application discovery process is used to identify all third-party and cloud vendor applications used within an organization as part of the Risk Assessment Process.
What is the Application Discovery?
The application discovery process is used to identify all third-party and cloud vendor applications used within an organization. An application is software used by an organization (e.g. Microsoft Word). An application vendor is the company or organization that provides the software (e.g. Microsoft).
Using the list you provide, Choice Cyber Security will identify and document the available security measures for each application. This can include measures such as (but not limited to):
- Two-factor authentication
- Single Sign-On
- Biometric Authentication
If applicable, vendor compliance is identified. This could include frameworks such as (but not limited to):
|
|
Types of Applications
We are looking for any cloud vendors and applications that access, store, process or transmit sensitive data. Be sure to include any of the following applicable vendors and applications as well as any company or industry specific resources:
|
|
Completing the Application Discovery Form
- Step 1: Download the application discovery template using the secure link provided below (or click here).
- Step 2: Open the file in your preferred spreadsheet application. Choice Cybersecurity recommends Microsoft Excel or Google Sheets.
- Step 3: Complete the Name column with the full name of each application used in your organization.
- Step 4: Complete the Usage column with what your organization uses the application for.
- Step 5: Complete the Sensitive Data Touched or Stored column with a description of the data that each application sends, receives, accesses, or stores. The more detailed the description, the more robust the application analysis can be.
- Specifically, clearly state the sensitive data an application interacts with, such as:
|
|
Here is a completed example:
| Name | Usage | Sensitive Data Touched |
| Zoom | Teleconferencing | Employee Credentials |
| Hubspot | CRM | Client Information, Client Email Addresses |
| Office 365 | General Company Documents, Employee & Client Email Addresses | |
| Stripe | Payment Processing | Client Billing Information, Client Credit Card Numbers, Client Email Addresses |